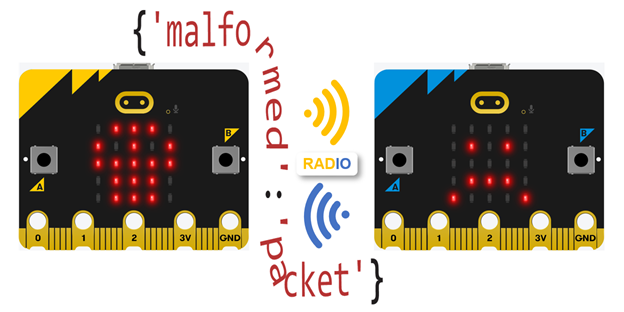
What it’s about
Devices on networks often communicate with software designed to send and receive messages that are encapsulated in packets. Packets typically contain information like the addresses of the sender and receiver and one or more messages. Examples include browser-server communication as well as phone-app-to-server communication. In such systems, sender and receiver software are designed to exchange packets in a compatible, expected format. But what happens when a packet is sent that is not in the correct format?
If new software or technologies are deployed that are not hardened against malformed packets, cyberattacks can end up exploiting their vulnerabilities. These kinds of attacks can cause a device or server to stop working. A malformed packet attack can even serve as a step toward gaining access to a network and its protected resources.
In this activity, you will use a pair of micro:bit modules communicating on a radio network to explore the kind of problems malformed packet attacks can cause. You will also learn how to update your scripts to prevent these kinds of attacks from interfering with your applications.
Before you start
You will need:
- Two or more micro:bit modules (on or off a cyber:bot)
- Two USB A to MicroB cables
- One or more computers with:
- Access to python.microbit.org
- An up-to-date Chrome or Microsoft Edge browser.
- A total of at least two available USB Ports. If you have two computers, each computer only needs one available port. If you have one computer, make sure it’s got two available USB ports.
- A micro:bit and a fully built and tested cyber:bot robot with their respective USB cables for the third activity:
- Malformed Packets and Keyboard cyber:bot Control
Complete these tutorials first:
- For all three activities
- Also required for the third activity:
After You Finish
You will be able to:
- Understand how online applications can be vulnerable to malformed packet attacks.
- Incorporate exception handling into applications to harden them against malformed packet attacks.
- Combine encryption and exception handling in an application to harden it against both sniffing and malformed packet attacks.
Preventing fellow students from successfully mounting a malformed packet attack on one of your micro:bit apps might be a key ingredient in winning a networked robot race. If you end up writing other software apps, the habit of testing for exceptions and incorporating exception handling into your apps can also help keep those apps safe from attackers.
